Understanding Token-Based Authentication: An Enterprise Perspective
As enterprises grow increasingly digital, therefore securing sensitive customer data while enabling seamless user experiences has become a top priority. Token-based authentication—a key pillar of modern identity and access management—plays a crucial role in this context. At ByteCraft Labs, we frequently assist our clients in designing robust architectures for secure user authentication and authorization. In this article, we’ll break down the sequence of token-based authentication, as illustrated in the diagram above, and demonstrate its application through an eCommerce use case.
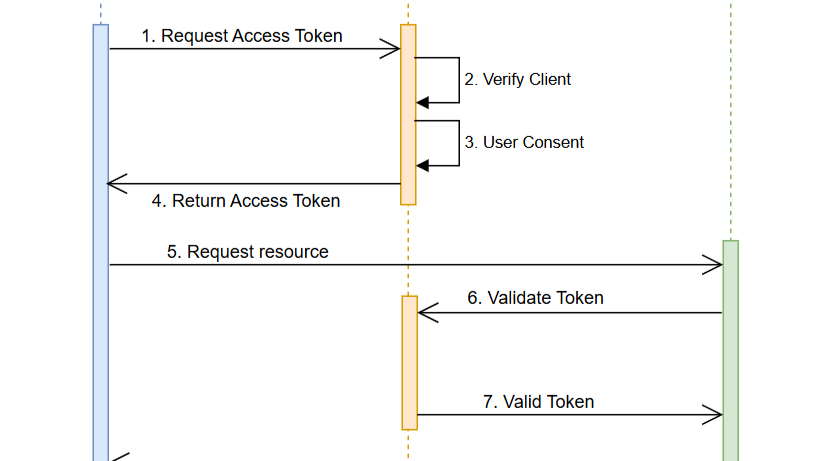
Step-by-Step Explanation of Token-Based Authentication
1. Request Access Token:
- The process begins with a BusinessClient (e.g., an eCommerce application) sending a request to the OAuth Server to obtain an access token. Then, the OAuth Server processes the request and returns the token.
- This request typically includes client credentials (like API keys) and user login information.
2. Verify Client:
- The OAuth Server verifies the BusinessClient’s credentials to ensure the request is coming from a legitimate source.
- If valid, the server proceeds to the next step.
3. User Consent:
- The OAuth Server prompts the end-user for consent. For instance, in our eCommerce example, the user might grant the application permission to access their purchase history or account details.
- Once consent is provided, the OAuth Server authenticates the user’s identity.
4. Returns Access Token:
- Upon successful authentication and authorization, the OAuth Server issues a unique access token to the BusinessClient.
- This token acts as a temporary “passport” that allows the BusinessClient to access resources on behalf of the user.
5. Requests Resource:
- Armed with the access token, the BusinessClient sends a request to the ResourceServer (e.g., a backend system managing user data) to access the desired resource.
6. Validate Token:
- Before granting access, the ResourceServer validates the token by contacting the OAuth Server to ensure it is authentic and hasn’t expired.
7. Valid Token:
- If the token is valid, the OAuth Server informs the ResourceServer, enabling it to proceed with the request.
8. Returns Resource:
- Finally, the ResourceServer retrieves the requested resource (e.g., user order history) and sends it back to the BusinessClient, thereby completing the process.
Token-Based Authentication in an eCommerce Context
To better understand this workflow, let’s explore a practical use case in eCommerce:
Scenario: A user wants to view their past purchases on an eCommerce platform.
1. The eCommerce platform (BusinessClient) requests access to the user’s purchase history by sending an access token request to the OAuth Server.
2. The OAuth Server verifies that the eCommerce platform is authorized to make such a request.
3. The user logs in and grants consent for the platform to access their purchase data.
4. The OAuth Server issues an access token to the eCommerce platform.
5. The eCommerce platform uses this token to request the purchase history from the ResourceServer.
6. The ResourceServer validates the token’s authenticity and checks if it has expired.
7. Upon validation, the ResourceServer retrieves the purchase history.
8. The eCommerce platform displays the purchase history to the user.
Key Benefits of Token-Based Authentication
- Enhanced Security: Tokens are short-lived and can be scoped to specific actions, reducing exposure.
- Scalability: Token-based systems are ideal for distributed architectures, supporting APIs and microservices.
- User Experience: Single sign-on (SSO) capabilities allow users to navigate multiple services without repeated logins.
Challenges and Best Practices
While token-based authentication provides robust security, implementing it correctly requires adhering to best practices:
- Always use HTTPS to encrypt communication.
- Implement token expiration and refresh mechanisms.
- Use secure storage for sensitive tokens.
- Regularly audit OAuth Server configurations.
Conclusion
Token-based authentication is more than a mechanism—it is a foundational component of secure, modern enterprise applications. At ByteCraft Labs, we empower businesses with tailored solutions to leverage the potential of such technologies effectively. By understanding the intricate workflow and adopting best practices, enterprises can safeguard their data and deliver seamless experiences to their users.
We’d love to hear your thoughts! How has token-based authentication transformed your application security strategy? Share your experiences in the comments below.
Design masterclass! The UI simplicity in Retro Bowl belies incredible strategic depth.